Certification Details
CompTIA Cybersecurity Analyst (CySA+)
Issuer: CompTIA
Credential ID: 0GW03KY5VB1EYMKJ
Validates the ability to apply behavioral analytics to networks and hosts for
threat detection, incident investigation, and
vulnerability management across SIEM/SOAR-driven environments.
- Threat detection, triage & response playbooks
- Security analytics (SIEM) & monitoring
- Vulnerability management & risk prioritization
- Incident reporting & post-incident improvements

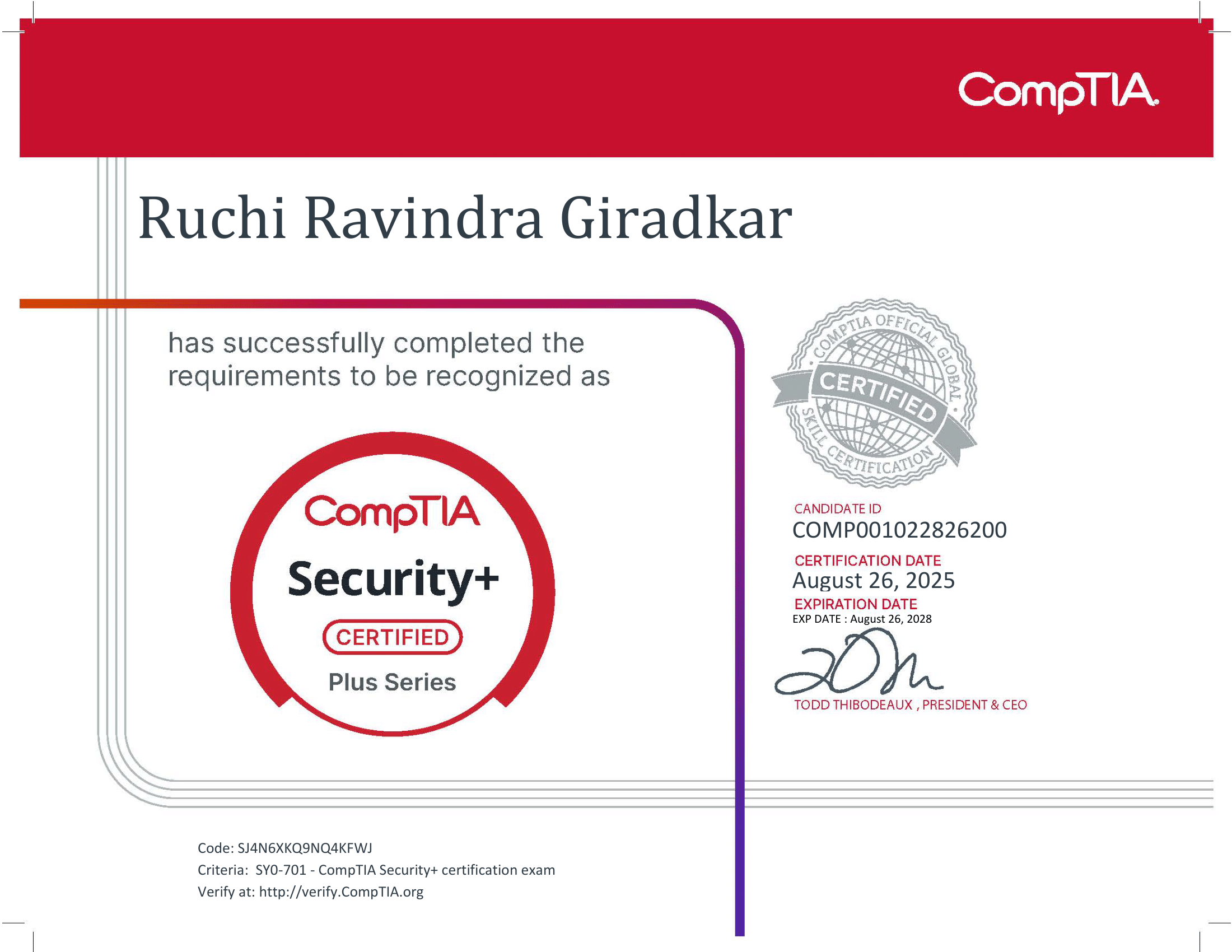
CompTIA Security+
Issuer: CompTIA
Credential ID: SJ4N6XKQ9NQ4KFWJ
Establishes a global baseline in core cybersecurity skills covering
secure architecture, risk management,
identity & access management, and incident response.
- Secure network & system architecture
- Threats, vulnerabilities & mitigations
- IAM, cryptography & PKI fundamentals
- Operations security & incident handling
CompTIA A+
Issuer: CompTIA
Credential ID: SGEQ8VB50EVESNY2
Validates IT support proficiency across hardware, operating systems,
troubleshooting, and basic networking & security.
- PC hardware, peripherals & storage
- Windows, Linux & basic OS administration
- Troubleshooting methodology & ticketing
- Networking basics & security hygiene

CompTIA Security Analytics Professional (CSAP) — Stackable Certification
Issuer: CompTIA
The CompTIA Security Analytics Professional (CSAP) is a
stackable certification for IT professionals with 2–5 years of experience
who want to specialize in cybersecurity analytics. It validates advanced expertise in
analyzing security data, detecting threats, and
managing incidents through data-driven insights. The CSAP credential is earned by
successfully completing both CompTIA Security+ and
CompTIA Cybersecurity Analyst (CySA+) certifications.
- Security analytics to detect threats & manage incidents
- Application security & behavioral analytics
- Access management, network security & risk management

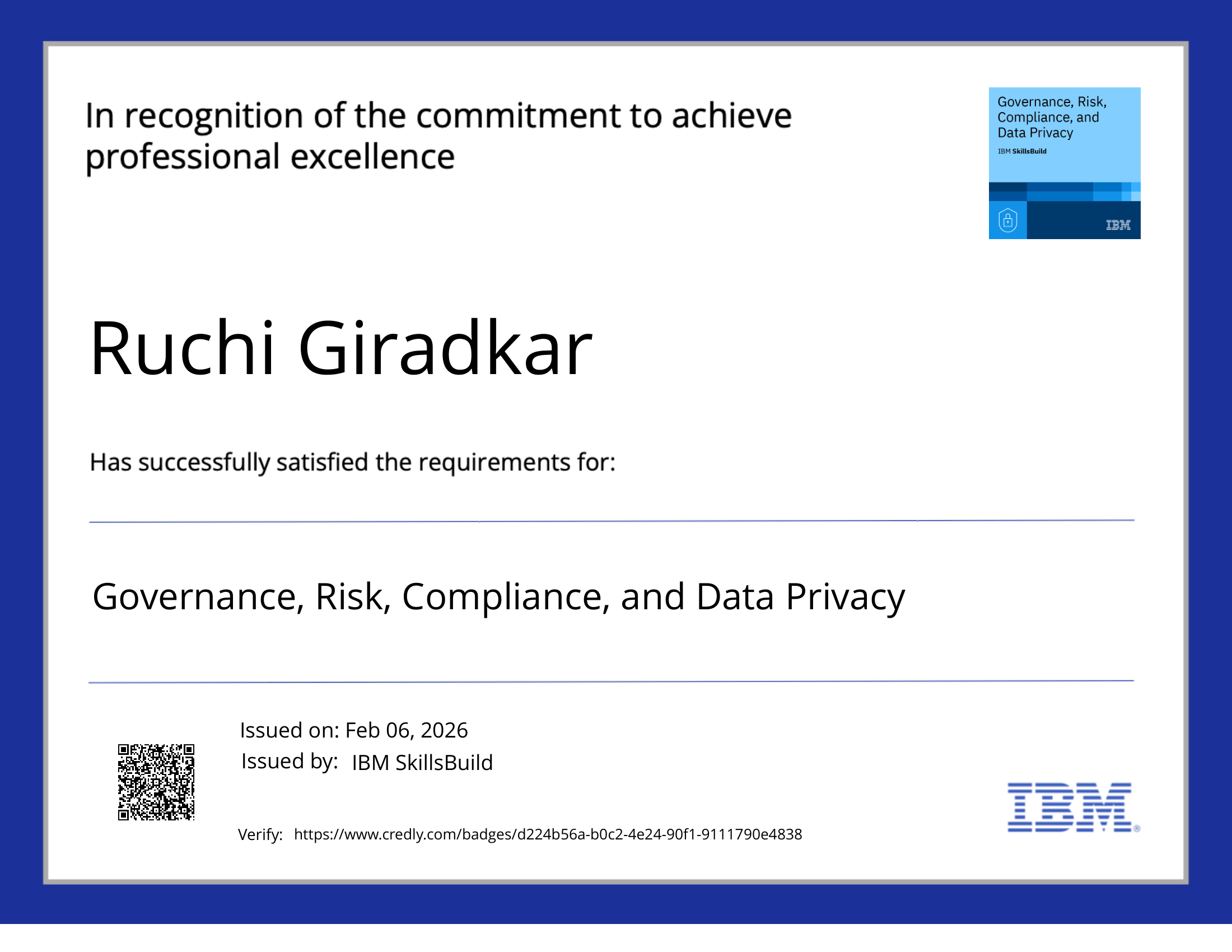
Governance, Risk, Compliance & Data Privacy
Issuer: IBM SkillsBuild
Digital Credential ID: CREDLY-8b3b8207-4adc-4568-bbb1-7c5cd0a1d5a4
Demonstrates applied capability to assess organizational data security posture and implement risk-based governance controls aligned with regulatory and operational requirements.
- Conduct enterprise risk assessments and map controls to compliance frameworks (ISO 27001, NIST-aligned practices)
- Design data protection strategies including encryption, backup, and access governance
- Support audit readiness through structured documentation, control validation, and continuous risk monitoring
Embedded Systems Security
Issuer: Riscure Academy
Hands-on training covering embedded system security with emphasis on
hardware attack surfaces, secure boot validation,
firmware integrity, and practical threat modeling.
- Embedded threat modeling & risk analysis
- Secure boot & firmware integrity validation
- Fault injection & side-channel attack awareness





