My Work
Cybersecurity Bootcamp Project
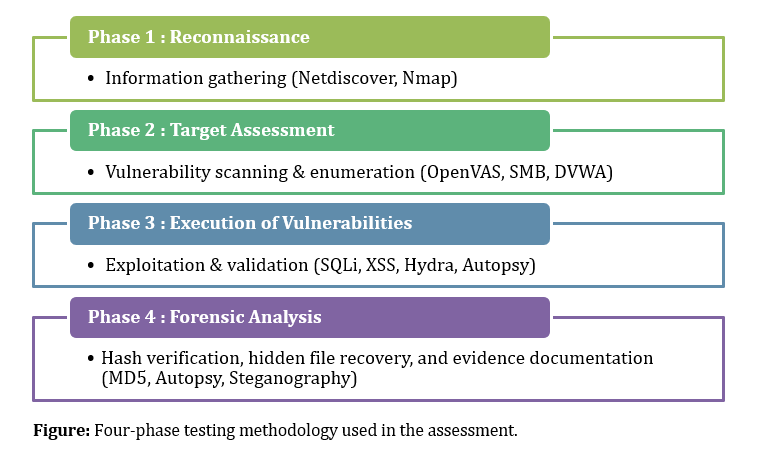
A full-scale Vulnerability Assessment, Penetration Testing (VAPT), and Forensic Investigation conducted during a 16-week Cybersecurity Bootcamp. The assessment uncovered 58 vulnerabilities (16 high-risk) and recovered 5 forensic artifacts from a simulated enterprise lab.
- Kali Linux
- Nmap
- Metasploit
- Hydra
- Greenbone (OpenVAS)
- DVWA
- Autopsy
Master Thesis
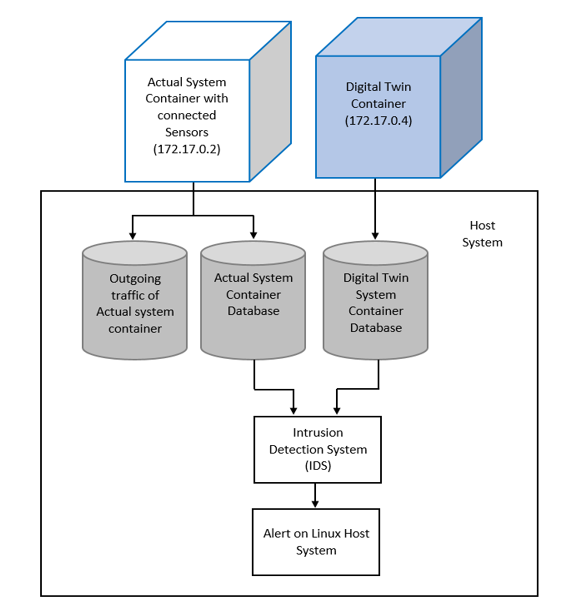
Digital Twin-based Intrusion Detection System (IDS),
Robert Bosch GmbH
Loction: Stuttgart,Germany
Designed and implemented a Digital Twin-based IDS during my Master’s thesis at Robert Bosch GmbH, enhancing real-time threat visibility and cyber resilience for Industry 4.0 environments using Docker and Python automation.
- Docker
- Python
- Shell Scripting
- Linux
- Network Monitoring
- Industrial IoT
Security & Privacy Specialist,
Continental Automotive Technologies GmbH
Loction: Regensburg,Germany
Performed Threat Analysis and Risk Assessment (TARA) aligned with ISO/SAE 21434 and UN ECE R155, designed secure architectures, and coordinated risk mitigation for embedded automotive platforms.
- ANSYS Medini Analyze
- ISO/SAE 21434 & UN ECE R155 Compliance
- Threat Modeling & Risk Mitigation
- Security Architecture Design
- Stakeholder Collaboration & Documentation

Bilingual Assistant Application Developer,
Fujitsu Consulting India
Loction: Pune,India
Built multi-channel UI features and mobile interfaces; translated Japanese technical documentation into performant, standards-compliant JavaScript and improved usability for enterprise clients.
- JavaScript / HTML / CSS
- UI & UX Optimization
- Japanese ↔ English Technical Translation
- Agile Development & Collaboration
- Performance Tuning & Testing

Trainee,
NTT DATA
Loction: Pune,India
Completed professional Java development training focused on object-oriented programming and application design fundamentals, plus Japanese language training (JLPT N4) for cross-border collaboration.
- Java & Object-Oriented Programming
- Software Design Fundamentals
- Project Lifecycle Understanding
- Japanese Language (JLPT N4)
- Cross-Cultural Team Communication

Skills
Technical Skills
- Security Operations & Incident Response: Security Monitoring · Alert Analysis · Incident Response Lifecycle (Detection · Analysis · Containment · Eradication · Recovery) · Zero-Day Vulnerability Triage (CISA · Log4Shell) · Business Impact–Driven Remediation · Ransomware Impact Assessment & Recovery · Risk-Based Incident Decision-Making · Digital Forensics & Evidence Handling · Incident Documentation
- Threat & Vulnerability Management: Vulnerability Assessment & Management (VAPT) · RCE & Ransomware Risk Evaluation · CVSS Risk Scoring & Prioritization · Asset & Inventory-Driven Impact Analysis · Affected System Identification · Ownership Mapping & Escalation · False Positive Reduction · Contextual Vulnerability Validation · Attack Surface Analysis
- Network, System & Platform Security: TCP/IP · Firewalls · IDS/IPS · VPNs · Linux Security & System Hardening · Security Baselines & Asset Monitoring · Container Security (Docker)
- Security Frameworks & Standards: NIST CSF · MITRE ATT&CK · ISO/IEC 27001 · ISO/SAE 21434 · UNECE R155 · OWASP Top 10 · GDPR · Threat Modeling (STRIDE · TARA) · Vulnerability Management Lifecycle
- Systems, Automation & Monitoring: Python (Defensive Security Automation) · PowerShell · Bash/Shell · Log Parsing & Script-Based Alerting · Incident Response & Recovery Automation · Prometheus · Grafana
- Security Tools & Platforms: Nmap · Wireshark · Tcpdump · Greenbone (OpenVAS) · Metasploit (Lab Use) · Hydra (Lab Use) · Autopsy · Docker · Kali Linux
- Collaboration & Communication: Technical Documentation · Security Workshops & Training · Stakeholder Communication · Risk Mitigation Planning · Cross-Functional & Cross-Cultural Collaboration (Germany / Japan / India) · Git · GitLab · SVN · Jira
Languages
- English: Fluent
- German: Level B1 (in progress)
- Japanese: JLPT N3 (Intermediate level)
- Hindi: Native/Fluent
- Marathi: Native/Fluent
Featured Cybersecurity Projects
Bosch Master Thesis
Digital Twin-based Intrusion Detection System for Industry 4.0 Connected Sensor
Key responsibilities and contributions
- Designed and implemented a Digital Twin based intrusion detection system for connected sensor environments
- Built containerized intrusion detection pipelines using Docker
- Simulated system behavior to detect anomalous and malicious activity
- Improved anomaly detection accuracy by approximately twenty five percent
- Implemented monitoring and visualization using Prometheus and Grafana
Capstone Project - VAPT & Forensic Analysis
Vulnerability Assessment | Penetration Testing | Digital Forensics
This project demonstrates an end to end offensive and defensive security workflow following real world security and incident response practices.
Project outcomes
- Identified fifty eight vulnerabilities across lab systems
- Classified findings into high, medium, and low severity based on risk impact
- Executed controlled exploitation including SQL injection, cross site scripting, weak credential attacks, and SMB misconfigurations
- Conducted digital forensic investigations including evidence acquisition, validation, timeline reconstruction, and chain of custody preservation
- Documented risks and remediation strategies in a professional reporting format
AIG - Cybersecurity Job Simulation
Security Operations | Zero-Day Response | Incident Response | Ransomware Recovery
Simulated real-world work performed by an Information Security Analyst within a Cyber & Information Security team, focusing on incident response, vulnerability management, and business-impact-driven remediation.
Experience highlights
- Performed zero-day vulnerability triage using CISA advisories to assess risk severity and remediation urgency
- Conducted infrastructure impact analysis and identified affected assets and system ownership
- Translated technical vulnerability details into clear, targeted remediation guidance for non-technical stakeholders
- Prioritized incident response actions based on business impact rather than technical exploitation
- Applied Python scripting in controlled lab scenarios to support recovery and defensive automation
Zero-Day Vulnerability Response (Apache Log4j / Log4Shell)
- Analyzed CISA-published zero-day advisories and assessed remote code execution (RCE) and ransomware risk
- Performed inventory-driven impact analysis to avoid false positives
- Distinguished vulnerable Log4j components from unrelated Apache httpd services
- Identified affected systems and responsible owners
- Drafted targeted remediation advisories including risk framing, patching guidance, and escalation steps
Ransomware Recovery – Controlled Lab Exercise
- Recovered encrypted archive access using Python (
zipfile.ZipFile) - Automated password discovery using a controlled wordlist
- Demonstrated disciplined recovery practices aligned with enterprise standards
- Documented recovery steps and defensive automation outcomes
Cybersecurity Process Audit Project
Governance Risk and Compliance | Security Controls | Risk Assessment
Project outcomes
- Conducted structured cybersecurity process and control audits
- Mapped security controls against ISO IEC 27001 and the NIST Cybersecurity Framework
- Identified control gaps and remediation priorities
- Documented findings suitable for management and audit review
Capstone Project - VAPT & Forensic Analysis
Vulnerability Assessment | Penetration Testing | Digital Forensics
This project demonstrates an end to end offensive and defensive security workflow following real world security and incident response practices.
Project outcomes
- Identified fifty eight vulnerabilities across lab systems
- Classified findings into high, medium, and low severity based on risk impact
- Executed controlled exploitation including SQL injection, cross site scripting, weak credential attacks, and SMB misconfigurations
- Conducted digital forensic investigations including evidence acquisition, validation, timeline reconstruction, and chain of custody preservation
- Documented risks and remediation strategies in a professional reporting format
Zero Trust Security Architecture – Enterprise Case Study
Zero Trust Architecture | Identity-Centric Security | Cloud & On-Premises | Data Protection | OT Security | Detection & Response
- Designed an enterprise-scale Zero Trust security architecture for a globally distributed hybrid environment, addressing identity-driven threats across cloud, on-premises, SaaS, remote users, and operational technology (OT).
- Defined architecture-level access enforcement, data protection, and centralized detection and response with a phased five-year roadmap prioritizing visibility, blast-radius reduction, and operational stability.
About Me

I am a Cybersecurity Professional with over 3+ years of experience assessing cyber risk across automotive and IT environments and translating security findings into actionable risk insights. My work centers on understanding attack surfaces, evaluating control effectiveness, and driving risk informed mitigation planning.
I have conducted structured threat analysis and cyber risk assessments across complex systems, working with engineering teams and suppliers to define mitigation priorities, inform risk acceptance decisions, and strengthen security alignment throughout the system lifecycle. With a background in software development and hands on experience in security monitoring and incident analysis, I bring technical depth grounded in how systems are designed and operated. I also bring international professional experience across Germany, Japan, and India, along with CompTIA CySA+, Security+ certifications, and am open to connecting with professionals working in cybersecurity.
View Academic RecordsGet in Touch
I am always open to connecting with professionals to discuss potential opportunities, exchange ideas, or explore areas of collaboration. If you would like to get in touch, please reach out through my LinkedIn profile using the link below.
Visit my LinkedIn





